FortiGate fundamentals and principles involve high security infrastructure and provide a secure set up to the client. FortiGate Firewall is the most respected and highly used security product in the market. It uses artificial intelligence and machine learning to achieve the latest security targets.
Fortinet covers many technologies within a single umbrella such as VPN, UTM, Security Profiles, FortiManager, FortiAnalyzer and many more.
Here, we will discuss all important features and technologies covered by Fortinet. Let’s start then…
Fundamentals of FortiGate Firewall
Below is the list of components supported by FortiGate. However, we have covered important components in this document.
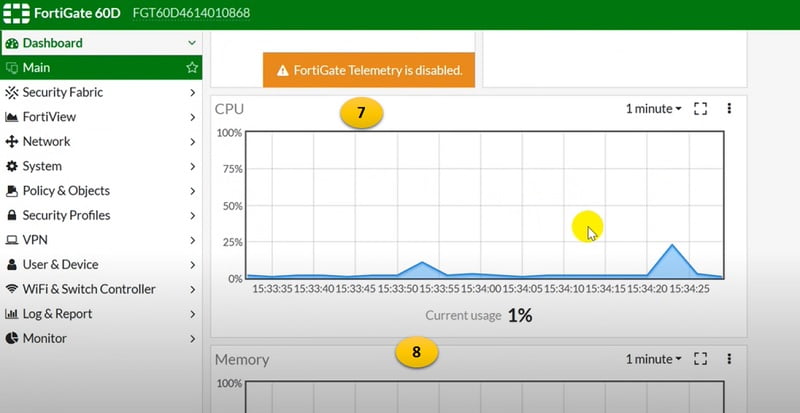
FortiGate Firewall Dashboard
FortiOS Dashboard consists of graphical view and stats of alerts. Widgets are static views of the FortiGate properties. It consists of:
- System Information contains hostname, IP address, Serial Number Firmware
- Licenses shows list of licences installed on the system and respective expiry date
- ForitCloud represents statistics of FortiCloud data
- Security Fabric shows summary of devices who have using Security Fabric feature
- Administrator all connected admin and their logged in time along with IP address
- CPU utilisation of device
- Memory, live utilisation of device
- Sessions shows number of sessions firewall is processing per second or minute
Other Widgets present in Dashboard
- HA status
- Log rate
- Interface Bandwidth
- Botnet Activity
- Advanced threat Protection
FortiGate Security Fabric
Fortinet Security Fabric involves different components that work together to secure the network.
Combination of below devices are required to create Security Fabric.
FortiGate Firewall
Firewall acts as a security component between ISP and downstream LAN devices. It secures networks from outside unknown attackers.
FortiAnalyzer
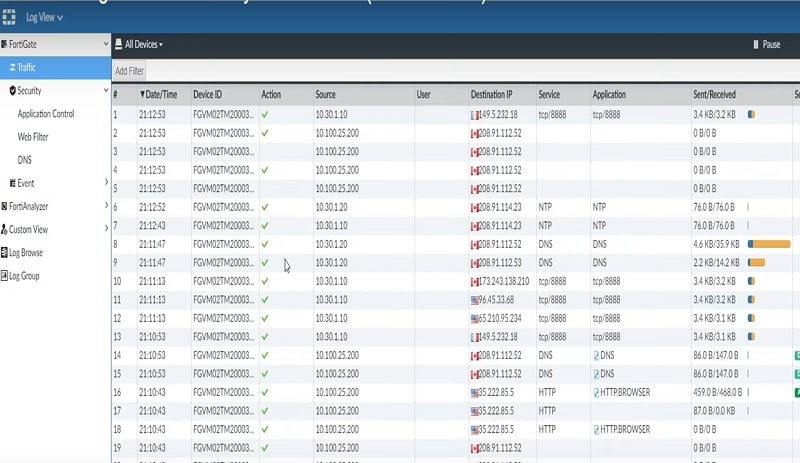
As its name defines, FortiAnalyzer can scan, monitor, collect logs of live traffic and create reports accordingly. It shows historical logs and events of any network which parse through the firewall.
FortiAnalyzer has below tabs available in the device to check logs:
- FortiView
- Threats
- Traffic
- Applications and Websites
- VPN
- System
- Security, Application Control, Web Filter, DNS
- Custom View
- Log Browse
- Log Group
LogView from FortiAnlyzer device:
FortiManager
FortiManager provides remote management to FortiGate Firewall. It uses port TCP 541 to communicate with the firewall.
FortiManager pushes Anti-virus, IPS and latest UTM updates from ForitManager to all connected devices.
FortiManager contains below tabs:
- Add Device
- Device Group
- Firmware
- License
FortiSandbox
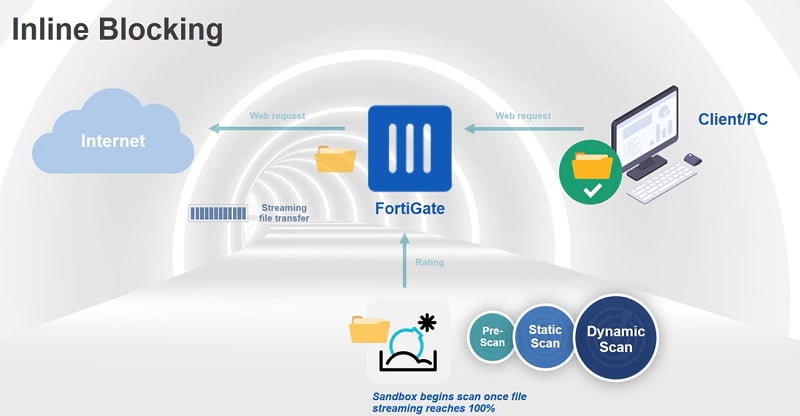
It is a cloud-based technology which generates the latest signatures based on malicious attacks. A FortiSandbox is a device that runs a sample in an isolated VM or cloud environment.
Copy of threat logs forward to FortiSandbox where it can check if the traffic has malicious content in it.
FortiSandbox has performed 3 types of scanning when receives any file from FortiGate
- Pre-Scan Group– it is the initial place where initial scan is performed by FortiSanbox. Several filtering is applied to the new file like pattern matching, checksum code sequence and TCP/IP attributes along with behavioural analysis of file/traffic pattern.
- Static Scan – Mainly deal with anti-virus and static AI scan. Antivirus is a traditional pattern matching feature however static AI scan uses machine learning to detect malware based on collected malware attributes from millions of samples.
- Dynamic Scan- It uses VM scan where the submitted file is processed in an isolated environment. Dynamic Scan also uses PEXBOX(code emulator) in which window files are parsed.
FortiSandbox Dashboard
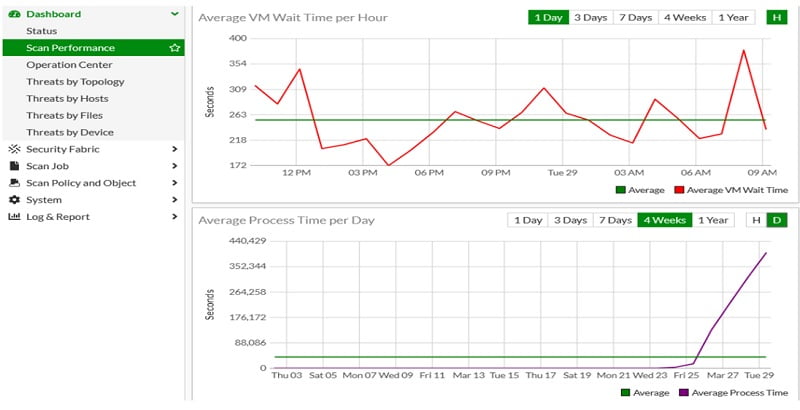
FortiADC
Application Delivery Controller is used to improve scalability of firewalls. It uses advanced server load balancer which routes traffic to available destination server based on the availability of backend server.
It helps to manage applications reliably, responsible and easy to manage.
ForiADC performs below task:
- Security
- Server Load Balancing
- Link Load Balancing
- Global Load Balancing
FortiADC benefits:
- Scale application with server load balancing feature
- Apply persistence with servers to maintain connection
- Reduce bandwidth needs and improve user QoE
- Provide redundancy and WAN optimization for applications
- We can apply traffic prioritization by applying QoS (Quality of Services)
- Improves SSL offloading win firewall for fast processing
Dashboard of FortiADC
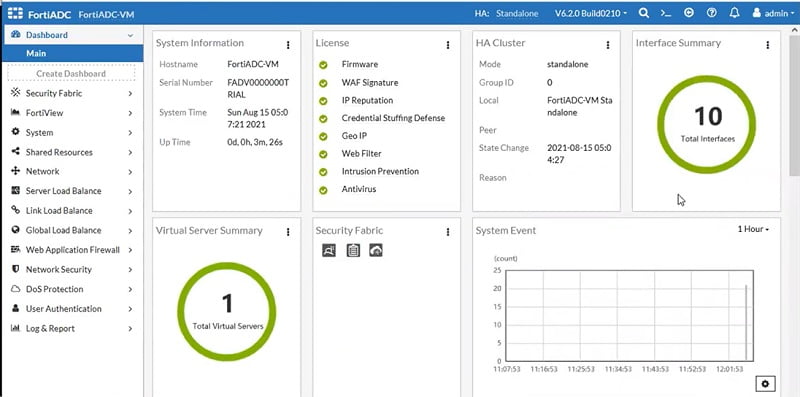
FortiAP
FortiAP units are thin wireless access points supporting the latest Wi-Fi technologies and easy deployment. For larger deployment FortiAP controllers can carry a dedicated wireless network and FortiAP models support a dedicated monitor to check radio signals.
FortiAP, FortiAP-C, FortiAP-S, FortiAP-W2, and FortiAP-U units are offered in a diversity of models to address particular use cases and management modes.
Wireless access points can be added in any network to provide wireless connection to users.
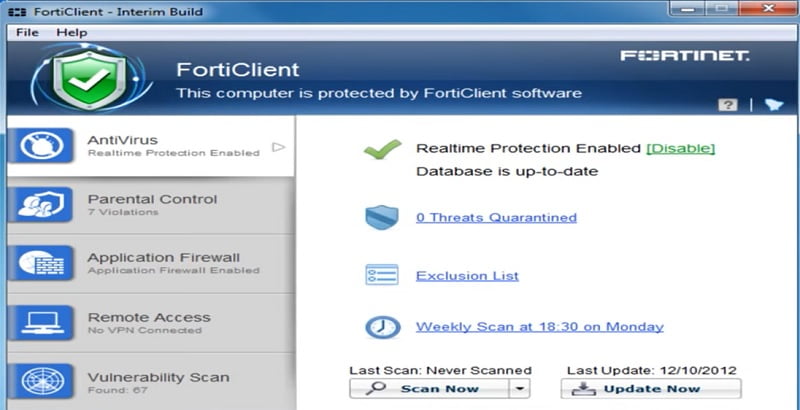
FortiClient
FortiClient is a VPN (IPSec and SSL) client just like Cisco AnyConnect. It can be used as an Anti-virus client and a host vulnerability scanners. Moreover it supports Web Filtering as well. In FortiGate you get at least 10 free licenses if you want to use those clients.
FortiClients helps to protect all the endpoints of your network including laptops, desktops and other devices.
These devices are either directly connected to your FortiGate devices or remotely connected through VPN.
- After admin set-up endpoint security on FortiGate , first time user with unregistered endpoints attempts to internet
- Captive portal will be displayed to download and install FortiCLient on the system.
- Once Installed FortiClient registered system to FortiGate
- Endpoint security profiles will be applient through FortiClient to local user system
- After successful registration windows PC will become a compliant endpoint.
FortiMail
FortiMail is a secure email solution which can provide a protection against inbound attacks , outbound attack , data loss issues in the network. As it captures email related threats like phishing, spamming, malware, zero-day attacks.
It protects emails from:
- Known and unknown threats
- Whaling Attack
- Spams
- Malicious link in email
4 types of modes used in FortiMail to protect emails from attack.
- Gateway Mode – FortiMail acts as an email gateway or a device which is used for Mail Transfer Agent. It fetches emails, scans the content and transfers it to the email server. Change in network topology will be required to implement FortiMail in the existing network.
- Transparent Mode – As the name specifies Fortimail acts as a Transparent proxy/device. It fetches the email, scans them and directly transfers it to the email server. No topology changes are required.
- Server Mode—It acts as a Local email server to the emails. It receives emails, scans it, and directly forwards them to users. Yes, topology change is required in the implementation of this mode.
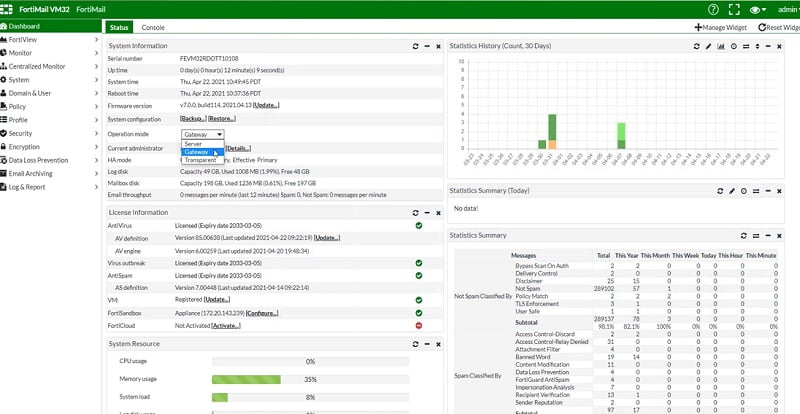
FortiGate VPN
FortiGate supports IPSec VPN and SSL VPN.
- SSL VPN – It is used for remote users to access applications from remote sites.
- Tunnel Mode- FortiClient VPN is required to install on users system to user system.
- Web Mode- Services are accessible via web-browser. But some applications and services are not supported.
- IPSec VPN – Site to Site tunnel needs to be created in the network to transfer data in an encrypted format.
- Site to site VPN initiated between to end points or physical devices
- IPSec Remote VPN also used in organizations to provide remote access to the Network by using remote VPN.
Security Profiles
Profiles which contain security features are known as Fortinet Security Profiles.
It includes below information about configuration.
- Anti-Virus: It identifies and block virus after scanning network traffic. FortiGate has offered two types of anti-virus features.
- Proxy-based: useful to mitigate suspicious malicious code.
- Flow-based: high performance based
- Web Filter: This feature takes action on internet URLs based on allow/block category in firewall. You can customize the URL Category in the firewall as well.
- Intrusion Prevention: It detects threat in network and mitigate malicious traffic in the network by applying signatures. We can create custom signatures as well.
Log and Report
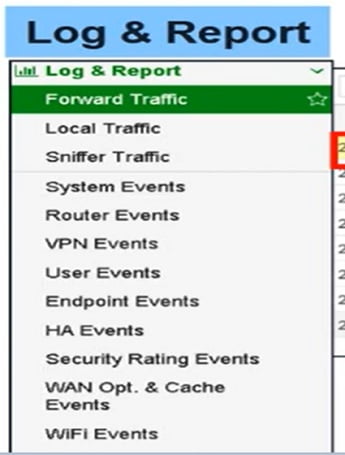
Logging and reporting are useful to check and understand any network logs. It covers event logs, system logs, VPN logs, threat logs, UTM logs and customized reports.
FortiGate supports several other log devices like FortiAnalyzer , Cloud, and syslog server.
Moreover, the log severity level is defined in every traffic log.
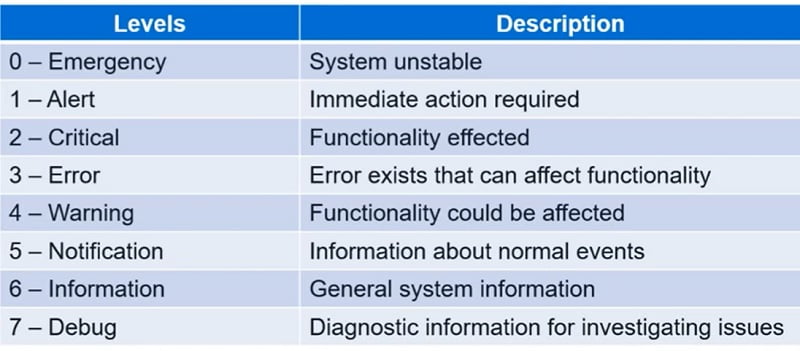
We can filter logs by using below options:
Conclusion
Fortinet brings high-performance network infrastructure security that ensures protection of any network, associated users, and components of traffic. FortiGate provides top rated solutions and centralized management systems to handle end to end security of an organisation.
No comments:
Post a Comment